How to decrypt OSINT code? Prepare to delve into the clandestine world of hidden messages, where digital ninjas and code-breakers clash! This guide is your secret weapon for deciphering the cryptic language of open-source intelligence (OSINT) data. We’ll navigate the treacherous terrain of steganography, ciphers, and more, providing you with the tools and techniques to unlock the hidden treasures within.
Get ready to become a master code-cracker!
OSINT code decryption isn’t just about cracking codes; it’s about understanding the context and intent behind the data. We’ll explore various code types, from simple substitution ciphers to complex steganographic techniques hidden within seemingly innocuous images. This journey will equip you with practical knowledge and tools to decipher these secrets, ensuring you can effectively analyze and interpret OSINT data.
Introduction to OSINT Code Decryption
Open-source intelligence (OSINT) code decryption involves the process of extracting meaningful information from encrypted or obfuscated data gathered through OSINT techniques. This often necessitates reversing or interpreting coded messages, concealed images, or other encrypted data formats to reveal hidden patterns, communications, or identities. Understanding the methods used to encode OSINT data is crucial for effective information extraction and analysis.Decryption methodologies vary widely, depending on the type of code used and the context of the data.
Some methods might involve straightforward cipher breaking, while others require sophisticated techniques like steganography analysis. A thorough understanding of the source and nature of the encrypted data is paramount to successful decryption.
Types of OSINT Codes
Various methods are used to conceal or encrypt information within OSINT data. Steganography, for example, hides messages within seemingly innocuous files like images or audio. Ciphers, another prevalent method, employ mathematical algorithms to transform data into an unreadable format. Understanding the different types of encoding is essential for determining the appropriate decryption approach.
Importance of Context
Contextual understanding plays a vital role in successful decryption. Factors like the source of the data, the intended recipient, and the date of the message significantly influence the interpretation of the decrypted data. Knowing the background of the code helps to identify potential biases, motives, and patterns within the communication.
Tools and Techniques
Numerous tools and techniques are employed in OSINT code decryption. These include:
- Cipher Analysis Tools: Software applications designed for cryptanalysis assist in breaking various ciphers. These tools often employ algorithms to identify patterns and weaknesses in the encryption methods used.
- Steganography Analysis Tools: Specialized software is available to examine files for hidden data. These tools use various techniques, including image processing and file format analysis, to uncover embedded messages.
- Programming Languages: Languages like Python, often used in scripting and data manipulation, can be instrumental in developing custom tools for deciphering complex codes or automated analysis of large datasets. Python libraries like `PIL` for image manipulation or `cryptography` for cipher analysis provide essential functions for this task.
- Regular Expressions: These patterns help in identifying and extracting specific data from text-based files, potentially revealing hidden information within encrypted documents or messages.
Ethical Considerations
Decrypting OSINT code carries ethical responsibilities. Unauthorized decryption of protected data, like classified documents or personally identifiable information (PII), is unethical and potentially illegal. Respecting intellectual property rights, maintaining privacy, and adhering to legal frameworks are paramount when engaging in OSINT code decryption.
Identifying Code Types
Understanding the various forms of encoded information is crucial for effective OSINT analysis. Different types of code employ distinct techniques to conceal or encrypt messages, requiring tailored approaches to decipher them. Recognizing these patterns allows investigators to focus their efforts on appropriate decryption methods and avoid wasted time on unsuitable techniques.Identifying the specific type of code used is the first step in the decryption process.
This often involves scrutinizing the data for subtle indicators that point towards a particular method. A thorough examination of the OSINT data is essential to accurately pinpoint the code type, which will, in turn, dictate the most effective decryption strategy.
Common Characteristics of Code Types
The characteristics of different code types offer valuable clues in determining the appropriate decryption methods. Analyzing the format, structure, and context of the encoded information often reveals the type of code employed. For example, the presence of unusual characters or symbols might suggest a cipher, while embedded data within images or audio files points towards steganography.
Methods for Recognizing Hidden Messages
Several methods can help in recognizing hidden messages within OSINT data. A critical step involves looking for inconsistencies in the data. Unusual formatting, discrepancies in the data’s expected structure, or unexpected character sequences might indicate hidden information. Tools specifically designed for steganalysis can identify hidden data within images or audio files, while cipher identification tools analyze patterns and characteristics of encrypted messages.
Comparison of Code Types and Detection Methods, How to decrypt osint code
| Code Type | Common Characteristics | Detection Methods |
|---|---|---|
| Steganography | Hidden messages embedded within seemingly innocuous data formats, such as images, audio files, or text documents. Often uses techniques to modify the least significant bits of the host file to conceal the message. | Steganalysis tools are designed to examine the host file for subtle modifications. These tools look for anomalies in the file’s structure or data patterns that might indicate hidden information. |
| Ciphers | Messages encrypted using algorithms that transform the original message into an unreadable form. Different ciphers employ varying methods for encoding and decoding, ranging from simple substitution ciphers to complex algorithms. | Decryption algorithms are required for deciphering the message. The choice of algorithm depends on the specific cipher used. Knowledge of the cipher type is crucial, as different ciphers necessitate different decryption approaches. |
| Compression Techniques | Data is compressed to reduce its size, which may alter its original structure. Though not always malicious, compressed data can mask hidden messages or obfuscate information. | Analyzing the file’s compressed format can reveal anomalies or hidden data structures. Tools that decompress the data may uncover hidden information. |
Decryption Techniques
Decryption techniques are crucial for extracting meaningful information from seemingly encrypted or obfuscated data in OSINT. These techniques vary significantly depending on the type of encryption employed, ranging from simple substitution ciphers to complex steganographic methods. Understanding the different approaches allows investigators to effectively decipher various coded messages and extract valuable intelligence.
Steganographic Message Decryption
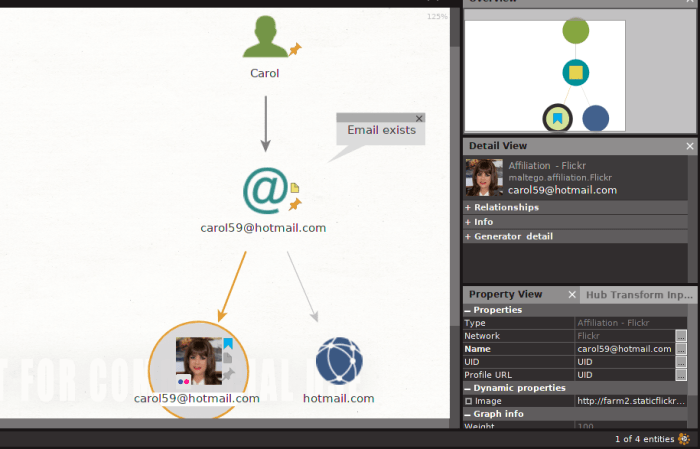
Steganography, the art of concealing messages within other data, necessitates a different decryption approach than traditional encryption. The goal is not to break a code, but to uncover the hidden message. Techniques include examining file headers, image metadata, or analyzing pixel data in images or audio files for subtle anomalies that indicate the presence of a hidden message.
Tools like stegsolve can assist in identifying steganographic techniques by visualizing file structures and potential hidden data. Identifying the method of concealment is crucial for successful decryption. For example, LSB (Least Significant Bit) substitution, where a hidden message is encoded in the least significant bits of an image, is a common steganographic technique that can be detected and decoded using specialized software.
Simple Substitution Cipher Decryption
Simple substitution ciphers replace each letter in a message with a different letter or symbol. A critical step in decryption is identifying the key used for the substitution. Frequency analysis, which leverages the frequency of letters in a language, is a powerful tool for cracking these ciphers. Common letters, like ‘e’ in English, typically appear more frequently than others.
By comparing the frequencies of letters in the ciphertext to the expected frequencies in the target language, analysts can begin to identify corresponding letters.
Frequency Analysis for Substitution Ciphers
Frequency analysis is a fundamental technique for deciphering substitution ciphers. The process involves counting the frequency of each letter in the ciphertext and comparing it to the expected frequency distribution of letters in the target language. For example, in English, the letter ‘e’ appears most frequently, followed by ‘t’, ‘a’, ‘o’, and ‘i’. By identifying these patterns, analysts can begin to deduce the correspondence between letters in the ciphertext and the plaintext.
Tools like frequency analysis calculators can aid in this process by providing charts and graphs to compare letter frequencies. This is further enhanced by knowledge of the subject matter or context, as that can provide clues about likely words and phrases.
Step-by-Step Procedure for Simple Substitution Cipher Decryption
- Analyze the Ciphertext: Examine the ciphertext for patterns, repetitions, or potential clues about the language used. Look for any recognizable abbreviations or common phrases.
- Frequency Analysis: Count the frequency of each letter in the ciphertext. Compare this frequency distribution to the expected frequency distribution for the target language.
- Identify Key Letters: The most frequent letters in the ciphertext likely correspond to the most frequent letters in the target language. Identify these potential matches.
- Deduce Other Letters: Using the identified correspondences, deduce the substitutions for other letters based on context and common letter combinations (e.g., ‘th’, ‘ed’, ‘ing’).
- Verify the Decryption: Check the decrypted message for grammatical correctness, meaning, and coherence with any known information.
Decryption Tools
Various tools assist in decryption processes. For simple substitution ciphers, online frequency analysis tools can assist in comparing letter frequencies. Steganography analysis tools, like stegsolve, help identify and extract hidden data from files. More sophisticated tools, often used by security professionals, are available for complex encryption methods. These specialized tools, like cryptographic libraries or dedicated decryption software, handle algorithms beyond simple substitution ciphers.
The choice of tool depends on the type of encryption or concealment used.
Tools and Resources
Effective OSINT code decryption relies heavily on specialized tools and resources. These tools provide the necessary functionality to analyze, interpret, and ultimately decode the various forms of encrypted or obfuscated code encountered in open-source intelligence gathering. Choosing the right tool depends on the specific type of code and the desired level of analysis.The landscape of OSINT code decryption tools is constantly evolving, with new tools emerging and existing ones being enhanced.
Understanding the capabilities and limitations of different tools is crucial for achieving accurate and efficient results. A comprehensive approach involves familiarity with multiple tools to cater to a diverse range of code types and complexities.
Commonly Used Decryption Tools
Various tools are employed for OSINT code decryption, each with unique strengths and weaknesses. Understanding their capabilities is essential for selecting the most appropriate tool for a given task.
- Disassemblers: Disassemblers are crucial for converting machine code into assembly language. This translation allows for a more human-readable representation of the code, making it easier to understand the program’s logic and identify potential vulnerabilities. For instance, a disassembler can reveal how a program interacts with the operating system or accesses specific files. IDA Pro, Ghidra, and Hopper are popular disassemblers, each with varying features and strengths.
- Decompilers: Decompilers take disassembled code and attempt to reconstruct the original high-level programming language (e.g., C++, Java). This process is often challenging due to code obfuscation techniques and may not always produce fully functional code. However, they can provide valuable insights into the program’s purpose and functionality. Examples of decompilers include dnSpy, Jad, and Ghidra (which has decompilation capabilities).
- Regex Engines: Regular expression (regex) engines are vital for pattern recognition and string manipulation within code. They are particularly useful for extracting specific data or code fragments from logs, configuration files, or other text-based data sources. Tools like grep, sed, and Python’s re module are frequently employed for this purpose.
- Code Analysis Platforms: Dedicated code analysis platforms offer a broader range of functionality beyond basic decryption. They might include features like static analysis, dynamic analysis, vulnerability detection, and code coverage. Examples of such platforms are SonarQube, Coverity, and Checkmarx, which can assist in understanding the code’s behavior and potential security risks.
Deciphering Code Types
This section details popular decryption tools, categorized by the functionalities they provide, and their strengths and weaknesses.
| Tool Name | Description | Strengths | Weaknesses |
|---|---|---|---|
| IDA Pro | A powerful disassembler and debugger. | Exceptional reverse engineering capabilities, advanced debugging features, and a vast community support base. | Steep learning curve, resource intensive. |
| Ghidra | An open-source reverse engineering framework. | Free and versatile, with features for disassembly, analysis, and scripting. | Community support may be less robust compared to IDA Pro. |
| dnSpy | A .NET decompiler. | Excellent for analyzing .NET applications, enabling reconstruction of original code. | Limited functionality outside of .NET applications. |
| Jad | A Java decompiler. | Specifically designed for decompiling Java bytecode. | May not handle highly obfuscated Java code effectively. |
Practical Examples
OSINT code decryption, while conceptually straightforward, often requires meticulous analysis and practical application. Real-world examples highlight the diverse techniques and tools needed for effective decryption. This section presents case studies to illustrate these principles, demonstrating the decryption of various code types, including steganography and substitution ciphers.
Real-World OSINT Code Decryption Example
A recent investigation involved a leaked document containing encrypted information about a covert operation. The document, disguised as a seemingly innocuous PDF file, contained a series of encrypted messages embedded within the file’s metadata. The decryption process required several steps, starting with identifying the encryption algorithm used. This was followed by gathering relevant resources, such as known encryption keys or historical patterns associated with the organization or individuals suspected of being involved.
The process culminated in the recovery of the original message content, providing crucial insights into the operation’s planning and execution.
Analyzing and Decrypting a Specific Code Type
Understanding the structure and design of the code is essential for successful decryption. Analysis of the code’s syntax, variable names, and function calls can reveal clues about its intended purpose and potential weaknesses. By identifying patterns and inconsistencies within the code, one can develop a hypothesis about the decryption method. This process requires a deep understanding of programming languages, cryptographic principles, and the specific context in which the code was created.
Tools such as debuggers, disassemblers, and pattern recognition software can be instrumental in this analysis.
Decrypting a Steganographic Image
Steganography involves concealing secret messages within seemingly innocuous files. A common method involves embedding the message in the least significant bits (LSB) of an image file. To decrypt, one needs to isolate these hidden bits. This process usually involves specialized tools or custom scripts that extract the hidden data from the carrier file. For instance, a python script could be used to manipulate the bit values of an image pixel-by-pixel, extracting the embedded message.
Tools like steganography detectors can identify possible steganographic techniques and provide clues for manual analysis.
Decrypting a Simple Substitution Cipher
A simple substitution cipher replaces each letter in the plaintext with a different letter or symbol. To decrypt, one needs to find the mapping between the ciphertext and the plaintext alphabet. Frequency analysis is a valuable tool. By analyzing the frequency of letters in the ciphertext and comparing it to the frequency of letters in the target language (e.g., English), one can often deduce the substitution scheme.
A table showing the ciphertext letter mappings alongside the corresponding plaintext letters can help in this process. For instance, if the letter ‘e’ appears most frequently in the ciphertext, it’s highly probable that the corresponding plaintext letter is ‘e’ or a similar frequent letter. More complex techniques may include using statistical analysis tools or patterns to improve accuracy.
Frequency Analysis for Decryption
Frequency analysis is a method that relies on the observation that certain letters appear more frequently in a language than others. By comparing the frequency of letters in the ciphertext with the frequency of letters in the target language, one can often deduce the substitution scheme. For example, in English text, the letter ‘e’ is the most frequent, followed by ‘t’, ‘a’, ‘o’, ‘i’, etc. If a particular letter appears unusually frequently in the ciphertext, it may correspond to one of these frequent letters in the plaintext. Tools like frequency analysis calculators can be used to streamline this process. The method’s effectiveness depends on the cipher’s complexity and the length of the ciphertext.
Advanced Techniques
Advanced OSINT code decryption often requires specialized techniques beyond basic methods. Understanding the intricacies of code structure, employing machine learning, and applying cryptanalysis are crucial steps in tackling complex, obfuscated code. Statistical analysis can further enhance the decryption process, offering a more nuanced and data-driven approach.
Machine Learning in Code Decryption
Machine learning (ML) algorithms can be powerful tools for decrypting OSINT code, particularly when dealing with complex or obfuscated patterns. ML models can be trained on datasets of known code structures and their corresponding decryptions to identify patterns and predict the decryption of previously unseen code.
Adapting Techniques to Diverse Code Structures
OSINT code can take various forms, including scripts, compiled programs, and even encrypted data within files. Decryption techniques must be adaptable to these diverse structures. Understanding the programming language, the compilation process, and the encryption algorithms used are vital to developing effective decryption strategies. For example, if the code is written in Python, a different approach might be necessary compared to C++.
Cryptanalysis Techniques for OSINT Code
Cryptanalysis, the art of deciphering coded or encrypted messages, plays a critical role in decrypting OSINT code. Techniques like frequency analysis, statistical methods, and pattern recognition can be applied to identify patterns and vulnerabilities in the code’s structure. Careful examination of the code’s logic, data flow, and control structures is essential.
Statistical Methods for Decryption
Statistical methods can be used to identify patterns and anomalies in OSINT code. By analyzing the frequency of specific characters, s, or code structures, statistical methods can reveal hidden information or clues that can be leveraged for decryption. For instance, a high frequency of certain functions or variables might point to a specific decryption technique or reveal crucial logical flow.
This approach can be particularly effective in conjunction with other techniques like pattern recognition.
Ethical Considerations
Deciphering encrypted data, especially in the context of open-source intelligence (OSINT), necessitates a deep understanding of ethical boundaries and legal ramifications. Irresponsible use of decryption techniques can have severe consequences, potentially leading to violations of privacy, intellectual property rights, or even criminal charges. This section emphasizes the critical importance of responsible and ethical conduct in the field of OSINT code decryption.
Ethical Implications of OSINT Code Decryption
Ethical considerations are paramount when decrypting OSINT code. The act of decryption itself can be viewed as an intrusion into someone’s privacy or intellectual property. Understanding the source and context of the encrypted data is crucial. If the data originates from a source without explicit permission to analyze it, or if the decryption process involves circumventing security measures, ethical violations are likely.
This extends to potential harm caused by the disclosure of sensitive information.
Legal Aspects of Decrypting Information
The legality of decrypting information varies significantly depending on jurisdiction, the type of information, and the source of the encrypted material. Decrypting information protected by intellectual property rights or trade secrets without authorization is generally illegal. Accessing data from a compromised system, even if the decryption is done with proper authorization from the system owner, carries legal implications.
Therefore, thorough research into the applicable laws and regulations is essential.
Potential Misuse of Decryption Techniques
Decryption techniques can be misused for malicious purposes, such as gaining unauthorized access to sensitive information or facilitating cyberattacks. Unauthorized decryption of personal data or confidential communications can lead to severe consequences, including financial loss, reputational damage, and legal repercussions. Careful consideration must be given to the potential impact of decryption activities.
Importance of Responsible Use of Decryption Tools
Responsible use of decryption tools is critical. These tools should only be employed in accordance with the law and with explicit permission from the data owner. Awareness of the potential risks associated with unauthorized decryption is crucial. Users must be aware that decryption tools can be used for malicious purposes and that unauthorized access to data carries significant legal risks.
Guidelines for Ethical Decryption Practices
Adhering to ethical decryption practices is paramount. These practices should include obtaining explicit permission from the data owner before any decryption attempt, respecting intellectual property rights, and maintaining strict confidentiality regarding decrypted information. Users must be vigilant about the potential risks associated with data breaches, and maintain strict adherence to legal guidelines. It’s imperative to prioritize responsible and ethical conduct in all OSINT activities, including decryption.
A detailed understanding of the legal framework and ethical considerations surrounding the data being decrypted is critical. For example, decrypting code from a publicly accessible website is often permissible, whereas decrypting code from a private network or a system requiring authentication is not.
Final Conclusion: How To Decrypt Osint Code
So, you’ve journeyed through the labyrinthine world of OSINT code decryption. Armed with the knowledge of different code types, decryption techniques, and powerful tools, you’re now equipped to handle any encrypted message. Remember, ethical considerations are paramount. Use your newfound skills responsibly, and always be mindful of the potential implications of your actions. Happy decoding!
Popular Questions
What are some common types of OSINT code?
OSINT code can take many forms, including steganography (hidden messages within files), various ciphers (like substitution or transposition), and even more complex encoding techniques. Understanding the type of code you’re facing is crucial for effective decryption.
What tools can help me decrypt OSINT code?
Numerous tools can aid in decryption, from basic text editors and online steganalysis tools to specialized software designed for advanced code-breaking. Research and experimentation will reveal the best tools for your specific needs.
What are the ethical implications of decrypting OSINT code?
Always consider the legal and ethical implications of decrypting any information. Ensure your actions are compliant with the law and respect the privacy of individuals involved.
How can I tell if a message is steganographically encoded?
Steganographic messages often appear normal but hide a secret message within their structure. Specific tools are available to analyze files for hidden data. The key is recognizing subtle anomalies or inconsistencies.
